Everything you need to protect WordPress content.

Gutenberg-aware block parsing
Analyzes content by correctly separating and reading structured Gutenberg blocks.
Postmeta & options analysis
Scans hidden post metadata and global options for malicious database injections.

Real-time reputation checks
Instantly verifies all external URLs against major threat databases like Safe Browsing and PhishTank.

Obfuscation & cloaking detection
Multi-layer decoding engine recursively unpacks Base64, URL encoding, ROT13, hex/octal chains, and serialized PHP data to expose hidden malware. Detects chained obfuscation techniques (eval→base64_decode→urldecode) that bypass signature-based scanners.
SEO spam pattern matching
Detects manipulative SEO tactics like hidden text, keyword stuffing, and malicious link patterns.

Incremental & scheduled scans
Runs resource-efficient partial scans automatically at scheduled times to monitor recent changes.

Non-destructive quarantine
Safely isolates infected data without deleting it, allowing for user review and precise restoration.

Revision-based rollback
Restores affected database entries to a clean, prior state using historical revisions.

Bulk operations
Allows users to process or clean multiple findings simultaneously, greatly speeding up remediation workflows.

Confidence scoring (0-100)
Rates each finding with a percentage score indicating the likelihood of it being malicious code.

Three-tier severity (Critical/Suspicious/Review)
Classifies all findings into one of three actionable categories: Critical, Suspicious, or Review.

Allow/deny list management
Controls which patterns are either always ignored or always flagged by the scanner based on custom user rules.

Auto-throttling & Safe Mode
Dynamically adjusts scan speed and activates a Safe Mode to prevent resource exhaustion on web hosts.
Chunked batch processing
Breaks large scanning or cleaning tasks into small, manageable batches to prevent timeouts and conserve resources.

Shared hosting optimization
Optimized resource usage specifically for the limits and constraints of shared hosting environments.

Multi-site support (coming soon)
Enables comprehensive scanning and management across all sub-sites within a WordPress Multi-site network.

Action Scheduler integration
Leverages the reliable Action Scheduler to manage and execute all background tasks efficiently.
Email alerts (immediate & digest)
Receives security notifications instantly or in a scheduled summary via email .
Webhook notifications
Sends real-time security alerts and data directly to external services via custom webhooks.
Admin dashboard widget
Displays an immediate, at-a-glance summary of all scanning activity and key security status on the main dashboard.
CSV/JSON export
Exports all scan data and findings into standard CSV or JSON formats for external analysis and reporting.

Multi-Layer Decoding Engine
Recursively decodes up to 3 layers of Base64, URL encoding, ROT13, hex, and octal obfuscation to reveal hidden malware. Catches sophisticated attacks that bypass traditional scanners by chaining encoding techniques.

Serialized Data Inspector
Safely unserializes and recursively scans PHP arrays in postmeta, options, and page builder data. Detects malware hidden in Elementor JSON, widget configurations, and complex nested structures up to 10 levels deep.

REST API (read-only)
Provides read-only access to all scan results and security findings for easy integration with external systems.

Scan summary reports
Generates comprehensive reports detailing scan results, actions taken, and the overall security status of the site.

Gutenberg-aware block parsing
Analyzes content by correctly separating and reading structured Gutenberg blocks.

Postmeta & options analysis
Scans hidden post metadata and global options for malicious database injections.

Real-time reputation checks
Instantly verifies all external URLs against major threat databases like Safe Browsing and PhishTank.

Obfuscation & cloaking detection
Multi-layer decoding engine recursively unpacks Base64, URL encoding, ROT13, hex/octal chains, and serialized PHP data to expose hidden malware. Detects chained obfuscation techniques (eval→base64_decode→urldecode) that bypass signature-based scanners.

SEO spam pattern matching
Detects manipulative SEO tactics like hidden text, keyword stuffing, and malicious link patterns.

Incremental & scheduled scans
Runs resource-efficient partial scans automatically at scheduled times to monitor recent changes.

Multi-Layer Decoding Engine
Recursively decodes up to 3 layers of Base64, URL encoding, ROT13, hex, and octal obfuscation to reveal hidden malware. Catches sophisticated attacks that bypass traditional scanners by chaining encoding techniques.

Serialized Data Inspector
Safely unserializes and recursively scans PHP arrays in postmeta, options, and page builder data. Detects malware hidden in Elementor JSON, widget configurations, and complex nested structures up to 10 levels deep.

Non-destructive quarantine
Safely isolates infected data without deleting it, allowing for user review and precise restoration.

Revision-based rollback
Restores affected database entries to a clean, prior state using historical revisions.

Bulk operations
Allows users to process or clean multiple findings simultaneously, greatly speeding up remediation workflows.

Confidence scoring (0-100)
Rates each finding with a percentage score indicating the likelihood of it being malicious code.

Three-tier severity (Critical/Suspicious/Review)
Classifies all findings into one of three actionable categories: Critical, Suspicious, or Review.

Allow/deny list management
Controls which patterns are either always ignored or always flagged by the scanner based on custom user rules.

Auto-throttling & Safe Mode
Dynamically adjusts scan speed and activates a Safe Mode to prevent resource exhaustion on web hosts.

Chunked batch processing
Breaks large scanning or cleaning tasks into small, manageable batches to prevent timeouts and conserve resources.

Shared hosting optimization
Optimized resource usage specifically for the limits and constraints of shared hosting environments.

Multi-site support (coming soon)
Enables comprehensive scanning and management across all sub-sites within a WordPress Multi-site network.

Action Scheduler integration
Leverages the reliable Action Scheduler to manage and execute all background tasks efficiently.

Email alerts (immediate & digest)
Receives security notifications instantly or in a scheduled summary via email .

Webhook notifications
Sends real-time security alerts and data directly to external services via custom webhooks.

Admin dashboard widget
Displays an immediate, at-a-glance summary of all scanning activity and key security status on the main dashboard.

CSV/JSON export
Exports all scan data and findings into standard CSV or JSON formats for external analysis and reporting.

REST API (read-only)
Provides read-only access to all scan results and security findings for easy integration with external systems.

Scan summary reports
Generates comprehensive reports detailing scan results, actions taken, and the overall security status of the site.
How do we compare to traditional security plugins?
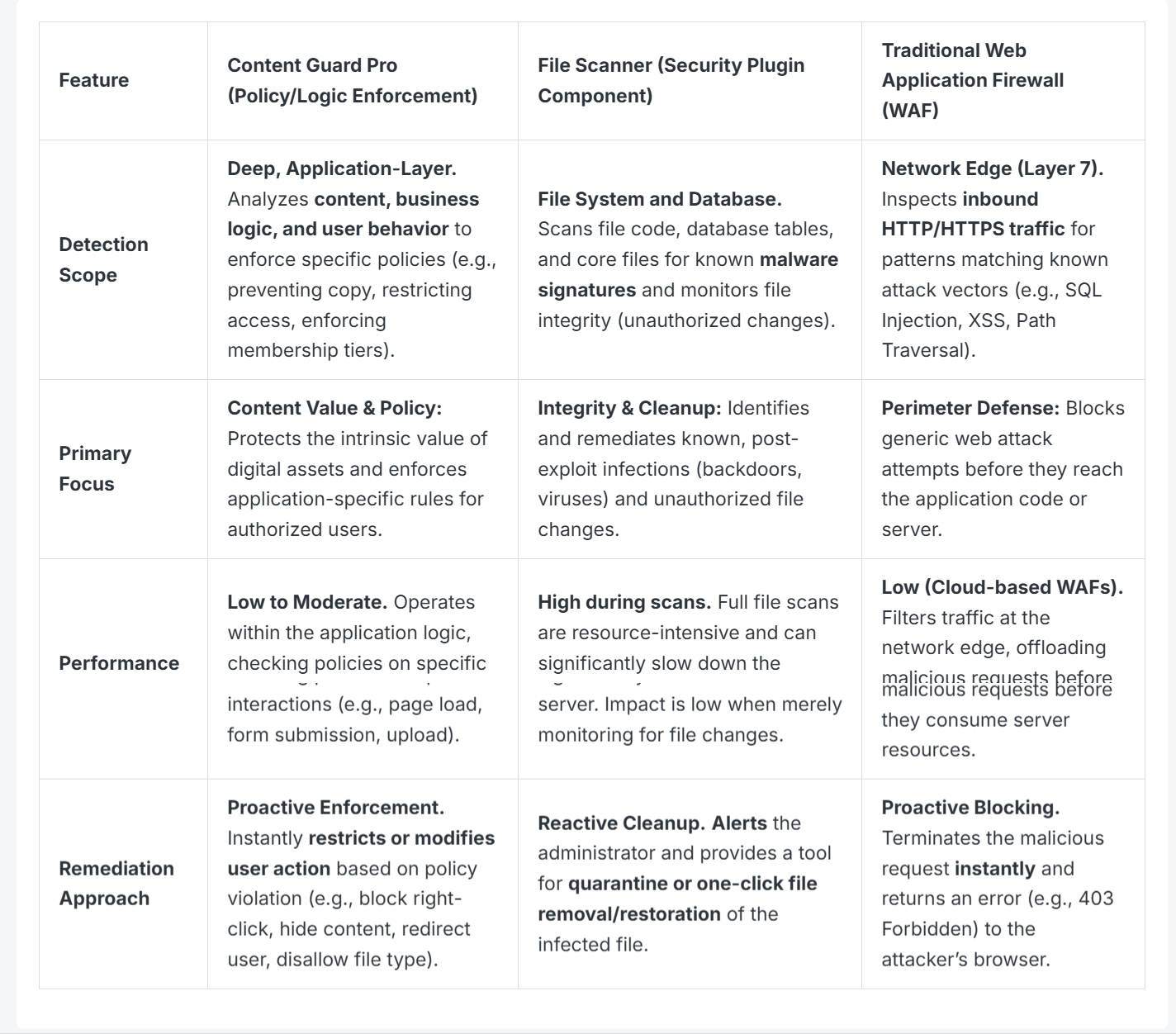
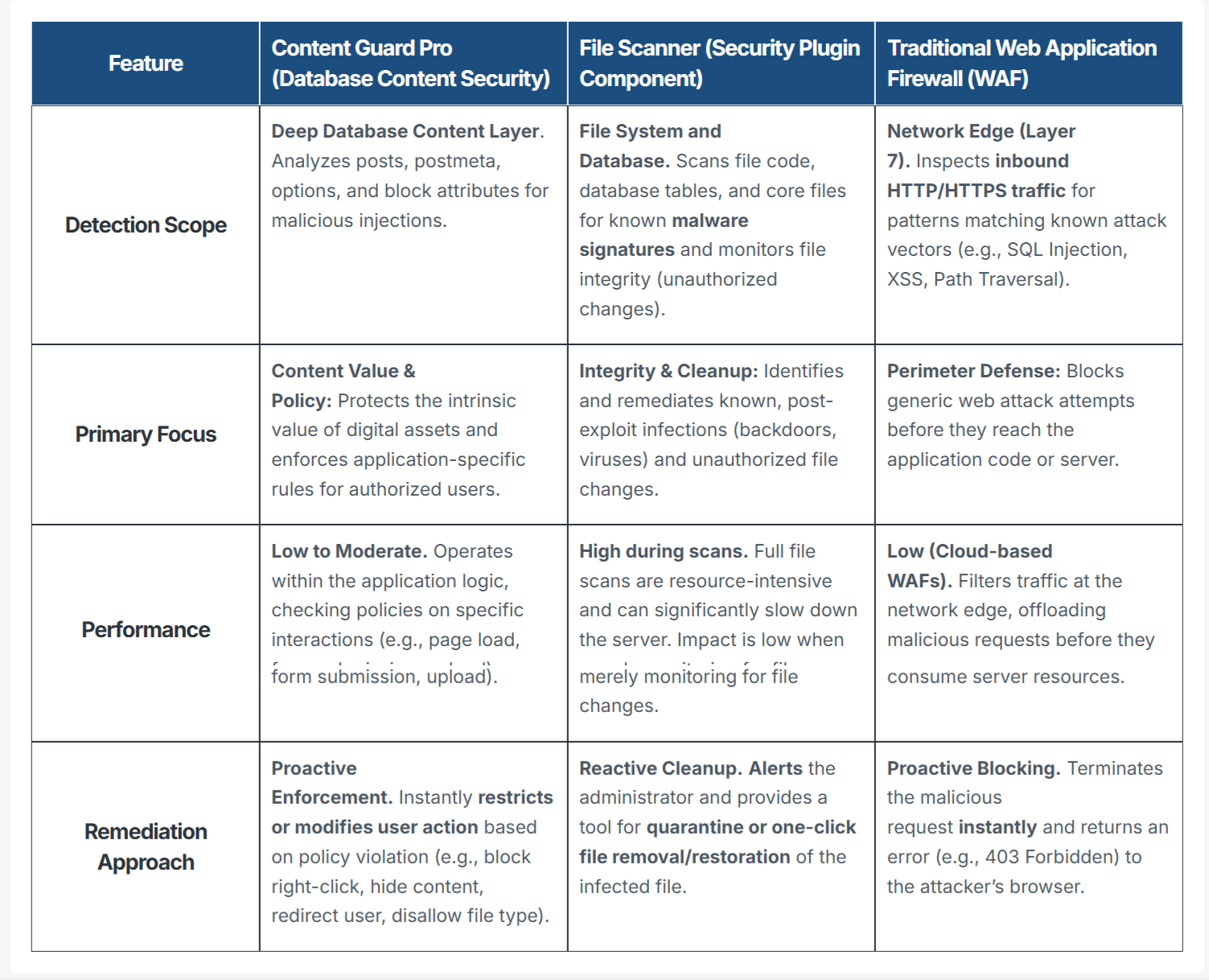
| Feature | Content Guard Pro (Database Content Security) | File Scanner (Security Plugin Component) | Traditional Web Application Firewall (WAF) |
| Detection Scope | Deep Database Content Layer. Analyzes posts, postmeta, options, and block attributes for malicious injections. | File System and Database. Scans file code, database tables, and core files for known malware signatures and monitors file integrity (unauthorized changes). | Network Edge (Layer 7). Inspects inbound HTTP/HTTPS traffic for patterns matching known attack vectors (e.g., SQL Injection, XSS, Path Traversal). |
| Primary Focus | Content Value & Policy: Protects the intrinsic value of digital assets and enforces application-specific rules for authorized users. | Integrity & Cleanup: Identifies and remediates known, post-exploit infections (backdoors, viruses) and unauthorized file changes. | Perimeter Defense: Blocks generic web attack attempts before they reach the application code or server. |
| Performance | Low to Moderate. Operates within the application logic, checking policies on specific interactions (e.g., page load, form submission, upload). | High during scans. Full file scans are resource-intensive and can significantly slow down the server. Impact is low when merely monitoring for file changes. | Low (Cloud-based WAFs). Filters traffic at the network edge, offloading malicious requests before they consume server resources. |
| Remediation Approach | Proactive Enforcement. Instantly restricts or modifies user action based on policy violation (e.g., block right-click, hide content, redirect user, disallow file type). | Reactive Cleanup. Alerts the administrator and provides a tool for quarantine or one-click file removal/restoration of the infected file. | Proactive Blocking. Terminates the malicious request instantly and returns an error (e.g., 403 Forbidden) to the attacker’s browser. |
How do we compare to traditional security plugins?
Feature
Content Guard Pro (Database Content Security)
File Scanner (Security Plugin Component)
Traditional Web Application Firewall (WAF)
Detection Scope
Deep Database Content Layer. Analyzes posts, postmeta, options, and block attributes for malicious injections.
File System and Database. Scans file code, database tables, and core files for known malware signatures and monitors file integrity (unauthorized changes).
Network Edge (Layer 7). Inspects inbound HTTP/HTTPS traffic for patterns matching known attack vectors (e.g., SQL Injection, XSS, Path Traversal).
Primary Focus
Content Value & Policy: Protects the intrinsic value of digital assets and enforces application-specific rules for authorized users.
Integrity & Cleanup: Identifies and remediates known, post-exploit infections (backdoors, viruses) and unauthorized file changes.
Perimeter Defense: Blocks generic web attack attempts before they reach the application code or server.
Performance
Low to Moderate. Operates within the application logic, checking policies on specific interactions (e.g., page load, form submission, upload).
High during scans. Full file scans are resource-intensive and can significantly slow down the server. Impact is low when merely monitoring for file changes.
Low (Cloud-based WAFs). Filters traffic at the network edge, offloading malicious requests before they consume server resources.
Remediation Approach
Proactive Enforcement. Instantly restricts or modifies user action based on policy violation (e.g., block right-click, hide content, redirect user, disallow file type).
Reactive Cleanup. Alerts the administrator and provides a tool for quarantine or one-click file removal/restoration of the infected file.
Proactive Blocking. Terminates the malicious request instantly and returns an error (e.g., 403 Forbidden) to the attacker’s browser.
Ready to try all features?
Free forever on WordPress.org | Pro plans from $69/year
